Install Outlook extension in Edge using MEM
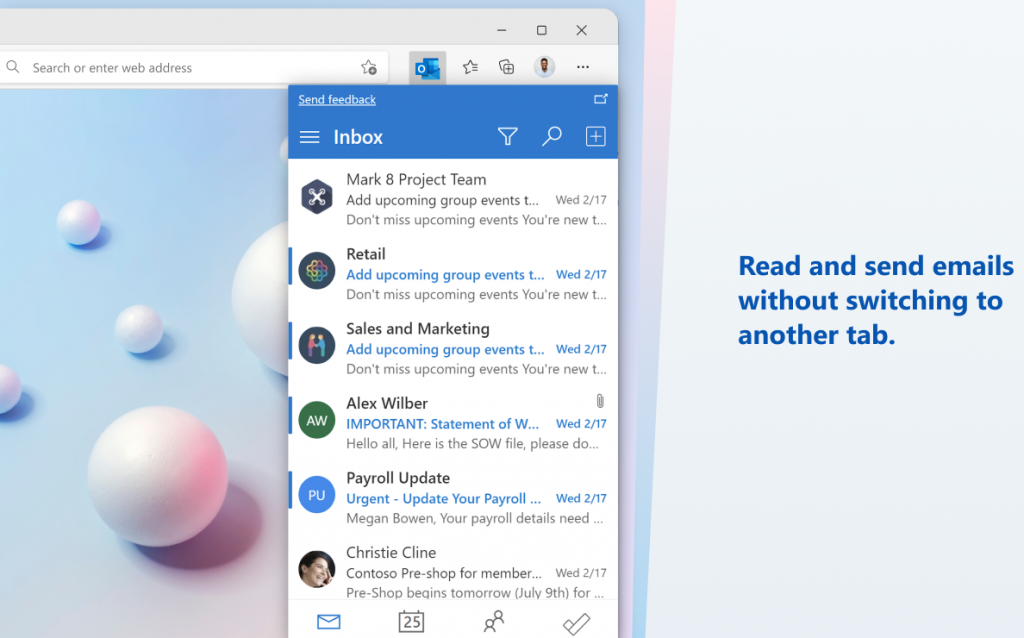
Microsoft has created a handy Outlook extension to Edge. You will be able to send and receive emails, use calendar and todo-list, all from the extension! The extension is currently in preview but seems to work well. In this blog we will have a look at how to distribute the extension using “Microsoft Endpoint Manger” […]
Install Outlook extension in Edge using MEM Read More »