How to disable WHfB DisablePostLogonProvisioning in Windows 11, using Microsoft Intune
Intro
Windows 11 is getting better by the minute and the latest additions are here. In this post we will have a look at the new control which will allow us to roll out (allow) Windows Hello for Business without the requirement to actually use it. All of this will of course be done by using Microsoft Intune.
💡Enabling this policy comes with a few downsides. Read on to learn more.
💡We have been able to use GPO to control this setting for some time and it is great to see an option for Entra ID-joined devices as well.
💡As pointed out here: PassportForWork CSP – Windows Client Management | Microsoft Learn it seems like the CSP only works for Insider builds, but I have had plenty successful tests on the 2024-05 build, it is possible this works on even earlier builds.
Why?
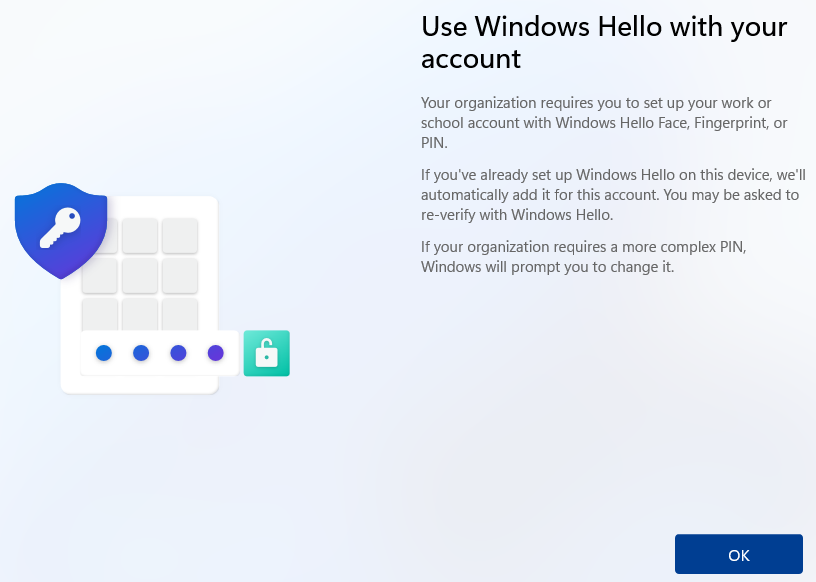
Disabling the first logon provisioning screen could make sense as users now can go to Windows Settings and pick a PIN/Biometrics/security key when they are ready to start using WHfB. It all comes down to allowing the user to decide when to start using WHfB.
We all know the struggle when the WHfB provisioning screen shows up after the first sign in (after Windows Autopilot), and the struggle gets real if the user doesn’t know what to do or how to actually use WHfB in a hybrid environment… we want to create as little confusion as possible after all.
The old way
If we enable Windows Hello for Business through an Intune policy, the user will need to add a PIN/BIO/security key at first sign in, before being able to start working. This could be a challenge if the user doesn’t know what to do or if the MFA setup has not been completed due to MFA not being enabled etc..
Windows Autopilot & Conditional Access
Keep in mind that the Windows Hello for Business provisioning, which happens directly after the user has signed in the second time during the Windows Autopilot flow, is really valuable as it allows for SSO if, conditional access is being used. This is often times overseen and could generate confusion.
If Conditional Access has been configured correctly we will get two MFA challenges before we can start working with our Autopilot device.
1️⃣ The first one is used to enroll the device to Intune and join Entra ID. This token is destroyed during the Autopilot provisioning flow due to security, as there could be two different users involved (one to enroll the device {enrolled by} and the actual user {primary user} of the device). Hence SSO cannot benefit from this specific sign in.
2️⃣ The second one is used by WHfB, after Windows Autopilot has completed.
If we disable WHfB provisioning, we will also remove the SSO opportunity and the user must manually sign in to one app before SSO kicks in, if conditional access is being correctly used.
💡This is because Windows itself doesn’t show the interactive sign-ins which requires MFA.
How?
As for now we must use a custom policy to control this specific setting.
PassportForWork CSP – Windows Client Management | Microsoft Learn
- Create a new custom Windows configuration profile
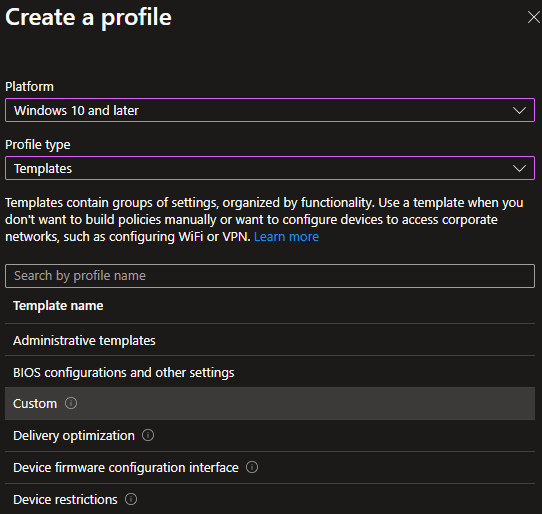
- Add a new row:
- Name: W11 – DisablePostLogonProvisioning
- OMA-URI: ./Device/Vendor/MSFT/PassportForWork/{TenantId}/Policies/DisablePostLogonProvisioning ❗(replace {TenantId}with your TenantId).
- Data type: Boolean
- Value: True
User experience
If this control is set to True we will not require WHfB provisioning at first sign in our users can decide when to start using it, but they will not get SSO to their apps.