Bad actors (internal and external) have so far been able to run brute-force attacks against local accounts in the dark, to try to find the correct password.
These attacks could be done by having physical access to the device but also by using RDP. But those days are over as the built-in local account lockout policy will block these attacks according to our settings.
Account lockout policy
The local account lockout policy comes with three controls and is typically applied by GPOs to AD/HAADJ devices. These settings are applied to managed accounts, but it is possible to apply them to the built-in administrator account as well (see step 4).
- Account lockout threshold: The maximum number of failed sign-in attempts before locking the account.
- Account lockout duration: Use this setting to determine how long do we want the account to be locked. The account will be automatically enabled after this time.
0 = an administrator must manually enable the account, no automatic enablement will be allowed. - Reset account lockout count after: Use this setting to configure the time-span between first failed sign-in attempt and when the account should be locked.
Example: If you set this setting to 10 and account lockout threshold to 5, the account will be locked after 5 failed sign-in attempts during 10 minutes. - Allow administrator account lockout: Is used to allow the built in local administrator account to be managed by these controls.
Default settings
Windows 11-22H2 has some default settings being applied from day zero.
| Account lockout threshold | 10 |
| Account lockout duration | 10 |
| Reset account lockout count after | 10 |
| Allow administrator account lockout | Enabled |
❗These settings are enabled by default on Windows 11-22H2 and newer. We must use policies to enable these settings on devices being upgraded from an earlier build.
Use Intune to configure account lockout settings
Let’s have a look at how to use Microsoft Intune to manage these settings.
The first thing we will notice is that we do not currently have any possibility to configure these settings by using settings catalog.
This is because controlling these settings by Intune are only available to Windows Insider builds and we must use CSP as for now.
We should see them added to the settings catalog soon enough! ✅
In my case I will run a PowerShell script as a Win32 app to configure:
- Account lockout threshold
- Account lockout duration
- Reset account lockout count after
And I will use a CSP policy to configure:
- Allow administrator account lockout
Let’s start with the PowerShell script
We can run the following command to view our current settings:net accounts
In my case I am running this on a W11-23H2 device which was originally installed as W11-22H2, so it should have these settings already configured, right?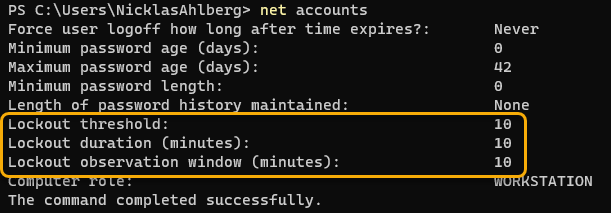
…and as we can see from above print screen it has the default settings which is great.
We can manually configure these settings by running below commands. This is great for testing but we will want to use Intune when it comes to running this on multiple devices.
net accounts /lockoutthreshold:15
net accounts /lockoutduration:15
net accounts /lockoutwindow:15
This is the result after running all three commands: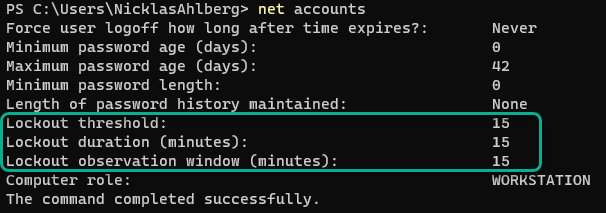
OK, so now we know how to change these settings. Let’s add the three commands to a PowerShell script and apply it as an app.
I always try to use PSADT as much as possible as it is great for logging and creating the detection method.
In this case I will just add the three commands to the ‘installation’ part and I will have it add a registry key and value for detection.
💡I want to apply the default settings (10) to make sure all devices are at the same level, only new installations of W11-22H2 or newer will have these settings out of the box, remember?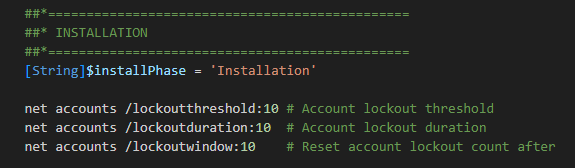
The whole application package is found here, feel free to use it.
I will use the Rock Enroll tool to wrap it to *.intunewin – this is already done if you downloaded the package from Github. You will find the file in the ‘_intune’ directory.
Now all we need to do is create the Win32 app in Intune:
- Create a new app
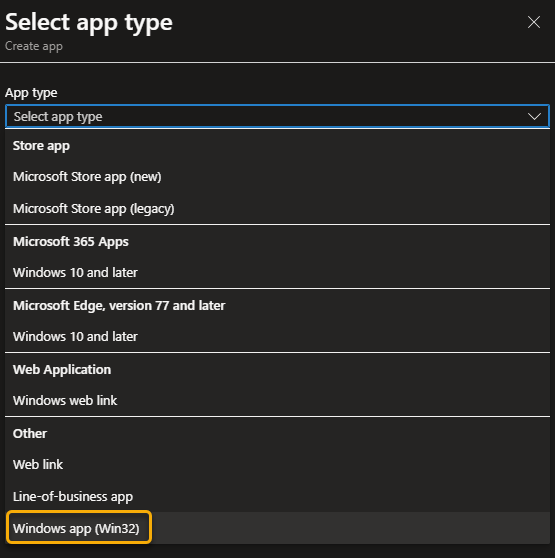
- App information
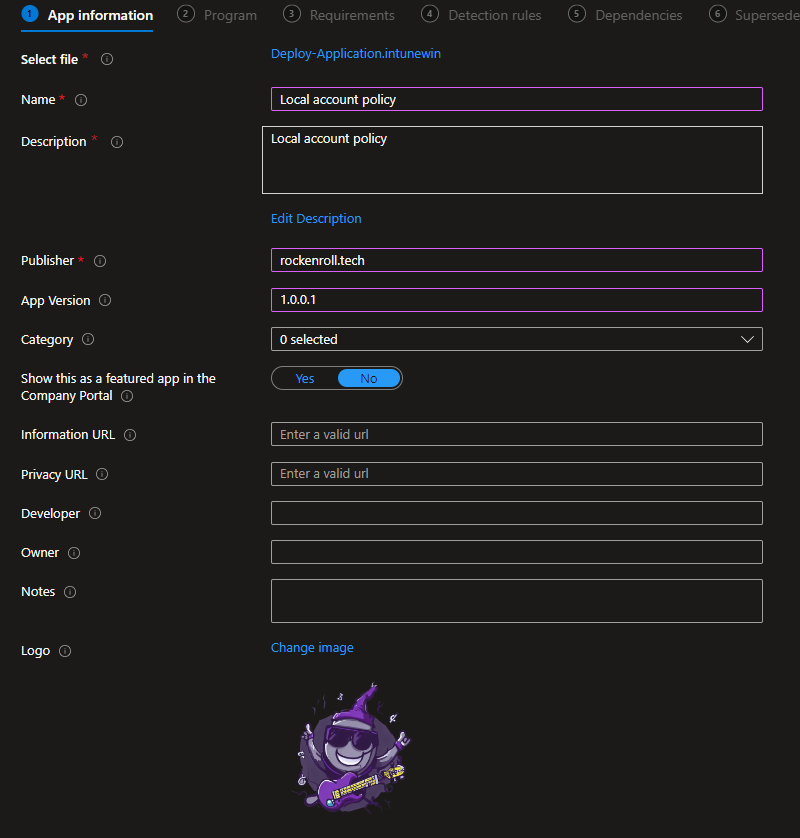
- Program
Install command: Deploy-Application.exe -DeploymentType Install
Uninstall command: Deploy-Application.exe -DeploymentType Uninstall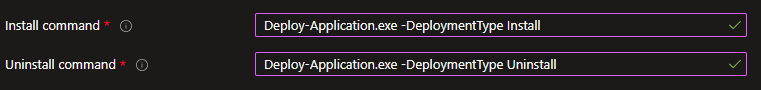
- Detection rules
Rules format: Manually configure detection rules
Rule type: Registry
Key path: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Rockenroll.tech\Detection\Local Account Policy
Value name: Version
Detection method: Version comparison
Operator: Greater than or equal to
Value: 1.0.0.1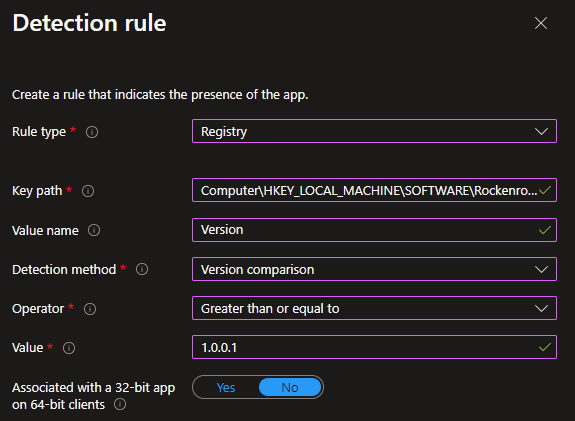
- If you downloaded the application package from Github the detection rule will measure against this value in the registry. You can change this by editing row 111: [string]$appDetectionVendor = ‘Rockenroll.tech’ in Deploy-Application.ps1 before uploading the package to Intune. Note that you must wrap it as a new .intunewin file before the upload.
- Now all we need to do is assign it to our devices and we are good to go.
Allow administrator account lockout
Let’s have a look at how to use Intune to configure “allow administrator account lockout” which means that we allow the lockout threshold, duration and reset counter to apply to the built-in administrator account as well.
❗As stated in the documentation this setting only applies to the built-in, well-known local administrator account and it doesn’t seem to apply to any manually created local administrator accounts. 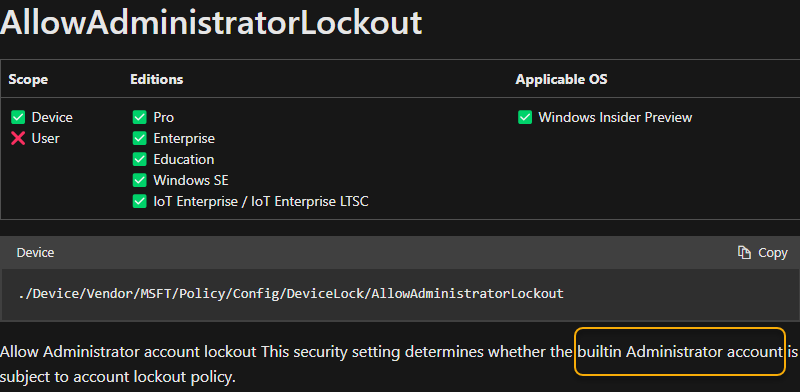
Same story here, this setting is enabled by default on new installations of W11-22H2 and must be manually enabled for all other devices.
This one is easier as we can use a CSP policy to configure it which is great news. This setting is part of the Windows 11 23H2 security baseline but as you might know, Intune has not been updated with the latest security baseline just yet.
- Add a custom configuration profile
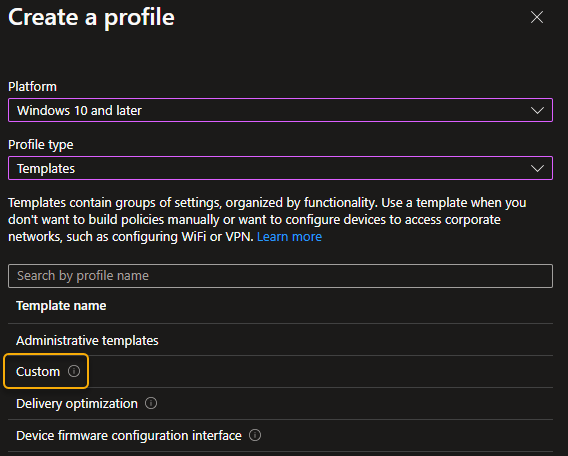
- Configuration settings
Name: Allow administrator account lockout
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/DeviceLock/AllowAdministratorLockout
Data type: Integer
Value: 1 - Assign it to your devices and you are go to go!
Demo
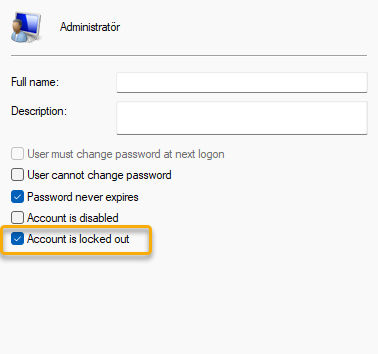
The account is going to be automatically unlocked after the lockout duration ⏳
Outro
So, now we have configured the account policies to make sure all of our devices are configured the same regardless of which OS-version they originate from.
I look forward to seeing the lockout threshold, duration and reset counter take part of the settings catalog as it makes sense to use Intune to configure those settings to make sure we can apply the brute-force protection to the built-in administrator account, regardless of device join-type (AADJ/HAADJ).
